Dynamic Entropy Decryption (DED)
In the ever-evolving landscape of cybersecurity, staying one step ahead of adversaries is a constant challenge. As part of the 2023 Ascension Project, ALS Cyber LLC created an innovation called Dynamic Entropy Decryption (DED). This technology has the potential to revolutionize how data is protected and decrypted. DED departs from traditional static encryption methods by introducing an element of adaptability and dynamic unpredictability into the encryption / decryption process. DED has several significant benefits and applications.
1. Security: DED provides an unprecedented level of security by continuously introducing randomness and unpredictability into the process. This makes it resistant to both brute-force and advanced cryptographic attacks.
2. Adaptive Defense: DED's LI enables it to adapt to evolving threats, learning from each decryption attempt and continuously improving its defenses.
3. Versatility: DED is applicable across various sectors, from securing sensitive government communications and financial transactions to protecting personal data in healthcare and e-commerce.
How Dynamic Entropy Decryption Works
Randomized Keys: Instead of using fixed keys, DED employs a dynamic approach, generating randomized keys. Three separate and distinctive dynamic keys are generated; one Dynamic Valid Key (DVK) and two Dynamic Invalid Keys (DIK) however, all three keys are used during the asynchronous process. This randomness adds an additional layer of complexity for potential attacks, making it exceedingly difficult to 1) select the DVK and 2) decipher / apply the DVK.
Entropic Reshuffling Process (ERP): DED incorporates an entropic reshuffling mechanism that constantly changes the order and arrangement of data blocks within the DVK and DIK. This dynamic shuffling renders conventional brute-force and pattern recognition attacks ineffective, as the key material structure is continually evolving during the process.
Learning Integration (LI): Integrated adaptive learning algorithms are integrated into DED, allowing the system to adapt and learn from previous decryption attempts. Over time, the system becomes increasingly adept at repelling attacks, enhancing security effectiveness.
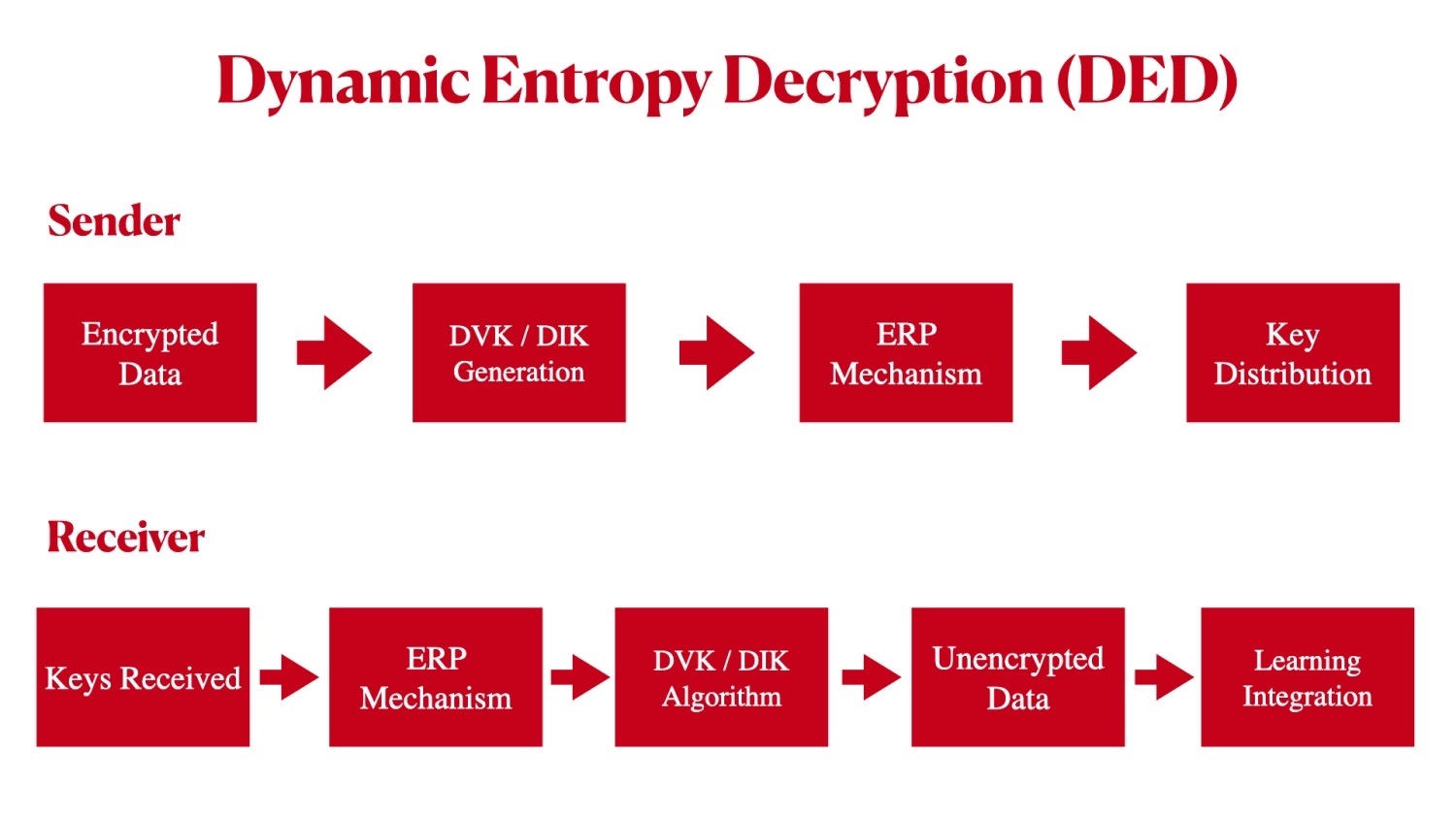
Explanation of the Schematic
This simplified schematic conveys the key elements of Dynamic Entropy Decryption, emphasizing the dynamic nature of the decryption process, the use of randomized keys, and the integration of adaptive learning for adaptability and improved security.
Encrypted Data (Ciphertext): This represents the data that has been encrypted using traditional encryption techniques, making it unreadable without the correct decryption process.
DED Decryption Algorithm: The DED Decryption Algorithm is at the core of the process. It's responsible for orchestrating the various components and operations involved in DED.
Entropy Reshuffling Process: This component continuously shuffles and rearranges the order of data blocks within the ciphertext. This dynamic shuffling introduces unpredictability into the decryption process.
Randomized Decryption Key Generation and Distribution: Instead of using fixed decryption keys, DED generates randomized keys for each decryption attempt. The randomness adds complexity, making it challenging for potential attackers to predict the decryption key.
Decrypted Data (Plaintext): The end result of the DED process is the decrypted data, which is in plaintext form and can be understood and processed as needed.
Learning Integration (Adaptive Learning): Learning algorithms are integrated into DED to adapt and learn from previous decryption attempts. Over time, the system becomes more adept at thwarting attacks and improving security.
Looking to the Future
While DED represents a monumental advancement in cybersecurity, it is not without challenges. The integration of DED into existing systems and widespread adoption will require careful planning. Additionally, ongoing research and development are essential to stay ahead of emerging threats such as quantum computing. In practice, DED involves complex mathematical and cryptographic operations, but this schematic provides a high-level overview of its functionality. ALS Cyber's DED holds the promise of significantly enhancing digital security in an age where data breaches and cyberattacks are rampant. By introducing adaptability, randomness, and dynamic learning into the process, DED offers a level of effective protection that is unrivaled by traditional encryption key methods.